Objectives
After completing this experiment you will be able to:
- Understand basic concepts about Wireless Sensor Networks (WSNs), types, applications of WSN
- Gain familiarity with LEACH, a cluster based routing protocol for WSNs
Time Required
Around 3.00 hours
Wireless Sensor Networks
A Sensor network is composed of a large number of sensor nodes that are deployed in a wide area with very low powered sensor nodes. The wireless sensor networks can be utilized in a various information and telecommunications applications. The sensor nodes are very small devices with wireless communication capability, which can collect information about sound, light, motion, temperature etc and processed different sensed information and transfers it to the other nodes.The following figure-01 illustrated the Wireless Sensor Network scenario.
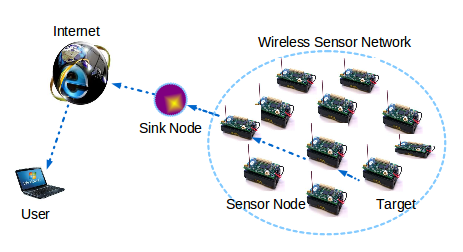 Figure-01: Illustration of Wireless Sensor Networks
Figure-01: Illustration of Wireless Sensor NetworksBasic Characteristics of WSNs
Wireless Sensor Networks are:
- Self-configuration, Self-healing, Self-optimization, and Self-protection capabilities
- Short-range broadcast communication and multi-hop routing
- Dense deployment and cooperative effort of sensor nodes
- Frequently changing topology due to fading and node failures
- Severe limitations in energy capacity, computing power, memory, and transmit power.
Operating Systems for WSNs
TinyOS operating system is specifically designed for WSNs. It is an event driven operating system. It also provides a programming frame-work for embedded systems. It has component-based execution model implemented in nesC. There are other operating systems developed for WSN like: SOS, CORMOS, EYES, PEEROS, MantisOS, Contiki, kOS, SenOS, Nano-RK, LiteOS.
Differences with Mobile Ad hoc Networks
We studied mobile ad hoc networks (MANETs), It is made up of a number of wireless mobile nodes. However, there are significant differences between MANETs and WSNs.
The number of sensor nodes in a sensor network is much more than that in an ad hoc network. Usually sensor networks consist of 1,000 to 10,000 sensor nodes covering the area.
Sensor nodes are generally static and cooperate together to transfer the sensed data.
In mobile ad hoc networks, the number of nodes are much less, but their mobility is very high.
Sensor nodes mainly use the broadcast communication paradigm, whereas most ad hoc networks are based on point-to-point communication.
Another difference between the two is that sensor nodes have a much lower power consumption requirement, of the order of 0.75 mW.
Types of Wireless Sensor Networks
Depending on the environment, there are different types of WSNs [i]
Terrestrial wireless sensor networks
- Ad-Hoc (unstructured)
- Preplanned (structured)
Underground wireless sensor networks
- Preplanned
- More expensive equipment, deployment, maintenance
Underwater wireless sensor networks
- Fewer sensor nodes (sparse deployment)
- More expensive than terrestrial
- Acoustic wave communication
- Limited bandwidth
- Long propagation delay
- Signal fading
Multi-media wireless sensor networks
- Sensor nodes equipped with cameras and microphones
- High bandwidth/low energy, QoS, filtering, data processing and compressing techniques
Mobile wireless sensor networks
- Ability to reposition and organize itself in the network
- Start with initial deployment and spread out to gather information
- Deployment, localization, self organizations, navigation and control, coverage, energy, maintenance, data process etc.
Routing protocols for WSNs
Many routing protocols have been proposed for WSNs. These have been classified into three categories, namely:
- Data-centric protocols
- Hierarchical protocols
- Location-based protocols
Data-centric protocols are query-based and use the concept of naming of desired data to eliminate many redundant transmissions.
Hierarchical protocols cluster the nodes so that cluster heads can aggregate and reduce the data to save energy.
Location-based protocols use position information to send the data to only the desired regions rather than to the whole network. The more important ones among these are SPIN, LEACH, PEGASIS, TEEN and APTEEN.
Clusters and Cluster heads in WSNs
Sensor nodes can be partitioned into a number of small groups, which is known as Clusters. These are the organizational unit for wireless sensor networks. Each cluster has the coordinator, called Cluster head (CH). CHs are required to organize activities in the cluster like data-aggregation.
Advantages of Clustering
- Transmit aggregated data to the data sink
- Reducing the number of nodes taking part in transmission
- Useful energy consumption
- Scalability for large number of nodes
- Reduces communication overhead for both single and multi hop
The LEACH Protocol
LEACH (Low-Energy Adaptive Clustering Hierarchy) is a cluster-based routing protocol for WSNs. It adapts the clustering concept to distribute the energy among the sensor nodes in the network. It improves the energy-efficiency of WSN beyond the normal clustering architecture. It uses a TDMA/CDMA MAC to reduce inter-cluster and intra-cluster collisions. As a result, we can extend the life time of our network, and this is the very important issue that is considered in the WSN field.
The following figure-02 illustrated the LEACH protocol with cluster nodes and cluster heads.
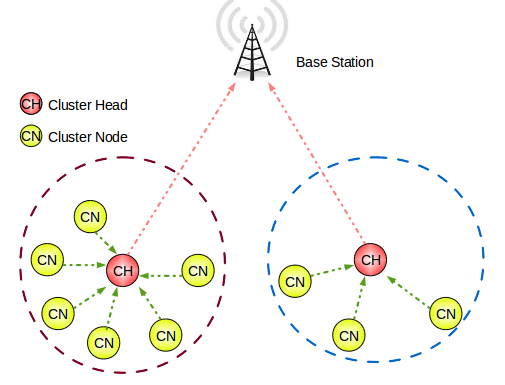 Figure-02: Illustration of LEACH Protocol
Figure-02: Illustration of LEACH Protocol Operation of LEACH
The operation of LEACH ([vii], [ix]) is divided into two phases:
Setup Phase (Where cluster-heads are chosen)
- Cluster-head Advertisement
- Cluster Set-Up
- Transmission schedule creation
Steady-state Phase (The cluster-head is maintained when data is transmitted between nodes)
- Data transmission to cluster heads
- Signal processing (Data fusion)
- Data transmission to the base station
The following figure-03 shows the above two functions of LEACH protocol
 Figure-03: Illustration of LEACH function with Setup and Steady State Phase
Figure-03: Illustration of LEACH function with Setup and Steady State Phase Algorithm for Setup Phase
Execute the following for each node
- Cluster-head Advertisement
- Let x be the random no between 0 and 1, n is the given node, P is the cluster-head probability, r is the current round, G is the set of nodes that were not cluster-heads the previous rounds.
- if x < T(n), then that node becomes a cluster-head. The threshold T(n) is determined ([viii]) as:

- Nodes that are cluster-heads in round 0 can't be again next 1/P rounds; after 1/P - 1, the threshold value will be T(n)=1
- In 1/P rounds, all nodes are eligible again to become cluster-heads
- After the election of cluster head, each nodes will broadcasts an advertisement message to the rest of the nodes by using a CSMA MAC protocol.
The algorithm is designed so that each node becomes a cluster-head at least once.
After the completion of this phase, each non-cluster-head node decides the cluster by using the received signal strength of the advertisement.
- Cluster Set-Up
- Each node informs the cluster-head node about its choice
- Each node uses CSMA- MAC protocol to transmit the information
- Cluster heads must keep receivers ON
- Transmission schedule creation
- Creates a TDMA schedule as per the number of nodes in the cluster.
- Each node send their data during their allocated transmission time to the cluster head
Algorithm for Steady State Phase
- Begin sensing and transmitting data to the cluster-heads.
- Then, the cluster-head node, receive all the data, aggregates it before sending it to the base-station.
- After a certain time, which is determined a priori, the network goes back into the setup phase.
Advantages of LEACH
- Increasing the lifetime of the sensor network.
- Self-organizing, adaptive clustering protocol that uses randomization to distribute the energy load among the sensors in the network.
- Distributed and no global knowledge of network required.
Drawbacks of LEACH
- LEACH assumes all the nodes to have same initial energy, which is not the case always in real-time problems
- It cannot be applied for mobile nodes, failure of cluster-heads creates a lot of problems
- It does not take into account that the systems might have multiple base stations.
- Extra overhead to do dynamic clustering.
Discussions on LEACH
One of the major drawbacks of LEACH is that the actual number of cluster heads formed per round is varying with respect to the desired number of cluster heads, specified as an input parameter to LEACH. Huafeng Liu,Liang Li and Shiyao Jin in their work on "Cluster Number Variability Problem in LEACH" [viii] had discussed about this problem, and proposed an improved clustering scheme (I-LEACH) as an improvement over LEACH. In the above work, they discussed the I-LEACH protocol in the following steps:
- Base station (BS) receives the aggregated data from the cluster heads. Therefore, it can be calculated that the number of nodes become the cluster head in the present round.
- Then the BS sends a broadcast message that contains the probability for the nodes to become the cluster head in the next round.
Applications of WSNs
The applications of WSNs are innumerable, since each sensor node is capable of monitoring a wide variety of ambient conditions such as temperature, humidity, lightning condition, pressure and noise levels. Below, we have given some typical application areas for WSNs. [i]
Military applications: Sensor nodes can be spread across a battlefield or enemy area and be programmed to track and monitor enemy troop movements or movement of terrorists and can be used to locate their exact positions.
Environmental applications: Sensor networks are being increasingly used for environmental concerns. Examples include tracking the nesting habits of seabirds by monitoring a large geographic region with human presence, or attaching the sensors directly to large mammals to monitor their behavior.
Monitoring of river currents is another application of WSNs, to measure their water inflow and mixture from various sources. Water-quality monitoring may also be useful to determine contamination with bacteria or other harmful pollutants.
the spread of sensor nodes across a forest to monitor temperatures and give early warnings of fire outbreaks. Weather prediction, climate monitoring, distributed computing, pollution tracking, seismic detection, detecting ambient conditions such as temperature, movement, sound, light, or the presence of certain objects, inventory control and disaster management are other similar applications.
Medical applications: WSNs can be used in medical applications by using the sensor node as a device that can reside on or within the human body and perform tasks that are currently done by costly machines. These include glucose monitors for continuous reading of insulin levels in diabetic patients; heart monitors for keeping track of the functioning of the heart, especially for patients with irregular heartbeats or coronary diseases; and artificial retinal and cortical implants to electronically transmit information to visually impaired persons.
Other medical applications include use in monitoring of human physiological data, tracking and monitoring doctors and patients inside a hospital and insurance cards.
Industrial applications: For use in industrial applications, low-cost sensor nodes could be attached to equipment to monitor performance. They could also be attached to parts as they move through an assembly pipeline on the shop floor. Thus, inefficiencies in plant process flow can be recognized quickly, rush orders could be expedited more easily and customer queries could be answered faster and more accurately.
Urban applications: WSNs can be used for various urban applications like transportation and traffic systems, auto-identification by driving license, parking availability, security monitors in shopping malls, parking garages, city streets and home security.
Some of the real applications are:
Volcano Sensor-web: This system has been used to implement a global surveillance program to study volcanoes. Sensor-web tests to study flooding, cryosphere events, and atmospheric phenomena.[ii] [iv]
Wireless sensor network system for landslide detection: This system is already in place at Anthoniar Colony, Munnar, Idukki, Kerala, India. [iii]
Simulating a WSN using Network Simulator 2
For simulating a WSN using NS2, a Mannasim simulator is required where LEACH script generator is available.
Mannasim is a open source Wireless Sensor Networks simulation environment comprised of two solutions:
- The Mannasim Framework
- The Script Generator Tool
The Mannasim Framework is a module for WSN simulation based on the Network Simulator (NS-2). Mannasim extends NS-2 introducing new modules for design, development and analysis of different WSN applications.
The Script Generator Tool (SGT) is a front-end for TCL simulation scripts easy creation. SGT comes blunded with Mannasim Framework.

 Introduction
Introduction Theory
Theory Simulation
Simulation Self-evaluation
Self-evaluation Procedure
Procedure Exercises
Exercises References
References

