Objectives
After completing this experiment you will be able to:
- Understand about Wi-Fi network, different standards, and related protocols
- Analyze the Wi-Fi communication range in the presence of the access point (AP) and the base station (BS)
- Learn about hidden node and exposed node problems, and their possible solutions
Time Required
Around 3.00 hours
Wi-Fi Networks
Wi-Fi (Wireless Fidelity) uses the IEEE 802.11 standard. Wi-Fi has some other extensions like 802.11a, 802.11b, and 802.11g. Wi-Fi technology operating at a frequency of 2.4 GHz and uses radio communication. [v]
IEEE 802.11 Standards
Following are the different standards for Wi-Fi [vi]
- 802.11 is the wireless local area networks (WLANs) standard. Supports 1- 2 Mbps.
- 802.11a is a high speed WLANs standard for 5 GHz band. It uses an orthogonal frequency division multiplexing (OFDM) encoding scheme.
- 802.11b is a wireless standard for 2.4 GHz band. It supports 11 Mbps. It uses only DSSS (Direct Sequence Spread Spectrum).
- 802.11d is a international roaming. This automatically configures devices to meet local radio frequency (RF) regulations.
- 802.11e address the quality of service (QoS) requirements for all IEEE wireless radio interfaces.
- 802.11f defines inter-access point communications for multiple vendor-distributed WLANs.
- 802.11g establishes an additional modulation technique for 2.4 GHz band. This supports speeds up to 54 Mbps.
- 802.11h supports the spectrum management of the 5 GHz band.
- 802.11i define the current security weaknesses for both encryption and authentication protocols.
- 802.11n supports more throughput improvements. Also provides speeds up to 500 Mbps.
The basic difference between 802.11a,802.11b and 802.11g are given below :
| Parameter | 802.11a | 802.11b | 802.11g |
|---|---|---|---|
| Standard approved | Sept 1999 | Sept 1999 | June 2003 |
| Available bandwidth | 300MHz | 83.5MHz | 83.5MHz |
| No. of overlapping channel | 4 | 3 | 3 |
| Frequency | 5GHz | 2.4GHz | 2.4GHz |
| Typical Data Rate | 23 Mbit/s | 4.5 Mbit/s | 19 Mbit/s |
| Maximum Data Rate | 54 Mbit/s | 11 Mbit/s | 54 Mbit/s |
| Range | 115 feet | 115 feet | 125 feet |
| Compatibility | None | None | backward compatible with b |
| Advantages | fast maximum speed, regulated frequencies prevent signal interference from other devices | lowest cost, signal range is good and not easily obstructed | fast maximum speed, signal range is good and not easily obstructed |
| Limitations | highest cost, shorter range signal that is more easily obstructed | slowest maximum speed, home appliances may interfere on the unregulated frequency band | costs more than 802.11b, appliances may interfere on the unregulated signal frequency |
Hardware Requirements for Wi-Fi
The following hardware devices are required for connecting the Wi-Fi Network.
Access Point
Access Point (AP) acts as a bridge between the wired network and wireless devices. It allows multiple devices to connect through it for accessing the network. An AP can also act as a router through which the data transmission can be possible from one AP to another.
Wireless Network Card
A wireless network card (WNC) is required on each device on a wireless network. A desktop computer would need an internal card, which will usually have a small antenna or an external antenna on it. These antennas are optional on most equipment and they help to increase the signal on the card.
Transmitter
Transmitter is used for emitting the wireless signals and it also receive the connection requests where a wireless client will send the requests and receives the replies from the transmitter. In this case, the transmitter is the wireless router.
How to connect to the Wi-Fi Networks?
Wi-Fi Network is easy to connect. Suppose, we will think about our laptop with any operating systems, then we can easily connect to a Wi-Fi network for accessing or we can share different files on a network.
Once we have acquired the necessary wireless networking hardware then, connect it all together to form a network and allow each device to communicate. The instructions below will act as basic guidelines of what needs to be done.
- The distance between each computer should be below 100 meters
- Each computer should be on the same floor
- Plug the AP into the power outlet and existing Ethernet jack on the network
- Configure the access point (usually through a web browser)
- Configure the client computers with the appropriate network settings required to be able to communicate with the AP.
Advantages of Wi-Fi
Following are the different benefits of Wi-Fi Networks
- In wireless ad-hoc network mode, devices like consumer electronics and gaming applications can directly connect and exchange data with each other.
- Digital images can be transferred wirelessly from cameras and other devices.
- All connected devices within the range have access to Internet and inter-networking.
- Wi-Fi enables wireless voice-applications (Vo WLAN or WVOIP).
- Wi-Fi provides a secure computer networking gateway, firewall, DHCP server and an intrusion detection system along with other features.
- Cost of cabling and network deployment of Local Area Networks is significantly reduced.
- Can be used at placed where wiring and cable lay-out is not feasible.
- Due to its cost effective nature, it can be used widely in different educational campuses and industries.
- Wi-Fi device can function in any type of geographical location.
Limitations
Like any other types of technology, Wi-Fi has its set of drawbacks that are listed as follows:
- Global inconsistency of spectrum assignments and operational limitations.
- Overlapping of channels.
- Limited range of equivalent isotropically radiated power in some areas.
- Greater power consumption compared to lower bandwidth standards.
- Limited battery life due to range and reach requirements.
- Wi-Fi network range is also limited.
MAC Protocols
The 802.11 standards use a MAC layer known as CSMA/CA (Carrier Sense Multiple Access/Collision Avoidance).
In CSMA/CA a Wireless node that wants to transmit & performs the following sequence:
1. Listen on the desired channel.
2. If channel is idle (no active transmitters) it sends a packet.
3. If channel is busy then, the node waits until the transmission end then a contention period where minimum time a host must transmit before it can be sure that the no other host’s packet has collided with its transmission.
4. If the channel is still idle at the end of the contention period, then the node transmits its packet otherwise it repeats the process defined in step-3 above until it gets a free channel.
The MAC header format shown in the figure-01 below: [vi]
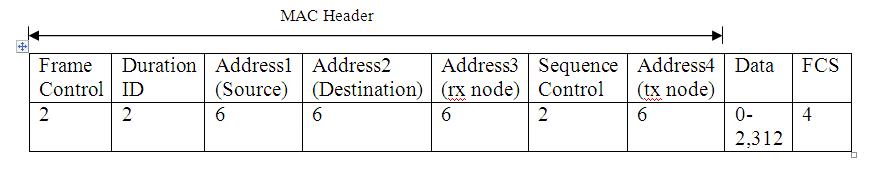 Figure-01: Illustration of MAC Header Format
Figure-01: Illustration of MAC Header FormatUse of RTS/CTS to Exchange Data
Step 1:
At first the sender check whether the medium is idle or not, if so, after the Distributed Inter Frame Space (DIFS will check the status and sense before transmitting the data in the wireless medium) units of time, it will broadcasts a Request-to-Send (RTS) frame to the receiver address.
Step 2:
If the receiver is within the range, then it will wait for Short Inter Frame Space (SIFS is the small time interval between the data frame and its acknowledgment) unit of time, then only it will respond to the sender with a Clear-to-Send (CTS) frame.
Step 3:
If the sender receive the CTS frame, then it will wait for another SIFS unit of time before sending the data frame to the receiver.
Step 4:
Finally, when the receiver will successfully receive the data frame, it will wait for SIFS unit of time and also send an Acknowledgement (ACK) message return to the sender.
Following figure-02 shows how data exchanges using RTC/CTS
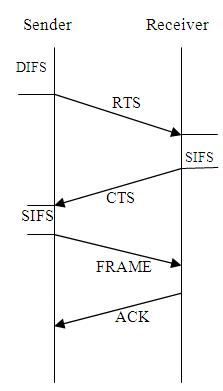 Figure-02:How Data exchanges using RTC/CTS
Figure-02:How Data exchanges using RTC/CTSIssues in Wi-Fi Networks
Wi-Fi suffers from two well known problems:
- Hidden Terminal Problem
- Exposed Terminal Problem
The Hidden Terminal Problem
The hidden node/ terminal problem found at a point to multipoint network and it is defined as being one in which three or more nodes are present. Let there are three nodes :node A, node B and node C.
A and C cannot hear each other.
A sends to B, C cannot receive A.
C wants to send B, C senses a free medium.
Collision occurs at B.
A cannot receive the collision.
A is hidden for C.
Figure-03 illustrates the Hidden Terminal Problem using node A,B and C
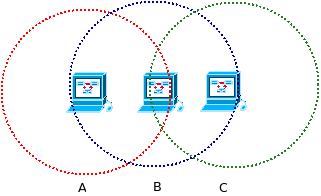 Figure-03: Hidden Terminal Problem
Figure-03: Hidden Terminal ProblemSolution of Hidden Terminal Problem
The solution of hidden terminal problem is as follows.
- When A wants to send a packet to B , A first sends a Request-to-send (RTS) to B.
- On receiving RTS, B responds by sending Clear-to-Send (CTS).
- When C overhears a CTS, it keeps quiet for the duration of the transfer.
- Transfer duration is included in both RTS and CTS.
- RTS and CTS are short frames, reduces collision chance.
The other methods that can be employed to solve hidden terminal problem are :
- Increase transmitting power from the nodes.
- Use unidirectional antennas.
- Remove obstacles.
- Move the node.
- Use protocol enhancement software.
- Use antenna diversity.
Effect of Hidden Terminal Problem
If one node hidden to another then the re-transmission will increase. It also increase the delay and decrease the throughput.
Exposed Terminal Problem
Suppose there are four nodes: node A, node B, node C and node D.
Here -
- B can send to both A and C .
- C can send to D, but not to A or B.
- A and C cannot hear each other.
Now the Problem as follows :
- When B transmits to A, C detects the transmission using the carrier sense mechanism.
- So C defers transmitting to D.
- But C could have sent to D, so blocked unnecessarily.
The following figure-04 shows the Exposed Terminal Problem using node A,B,C and D
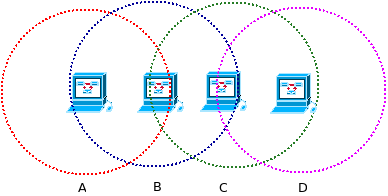 Figure-04: Exposed Terminal Problem
Figure-04: Exposed Terminal ProblemSolution to the Exposed Terminal Problem
Exposed terminal problems cannot be mitigated with RTS/CTS. This can be explained with the following scenario.
- Suppose B sends RTS to A.
- A sends CTS to B.
- C hears RTS, but not CTS, assumes it is ok to send to D.
Simulating a Wi-Fi using Network Simulator 3
NS-3 is an open source network simulator, and supposed to be the future replacement of NS-2. We would be using NS-3 for this experiment. Providing a tutorial on NS-3 is, however, outside the scope of this experiment. The Exercises section presents two problems and their solutions using NS-3. We would use the existing codes and tweak it to get familiarized with the basic characteristics of Wi-Fi. Nevertheless, one could visit the NS-3website to learn more about this simulator.

 Introduction
Introduction Theory
Theory Simulation
Simulation Self-evaluation
Self-evaluation Procedure
Procedure Exercises
Exercises References
References

