Objectives
After completing this experiment you will be able to:
- Learn about Local Area Network (LAN); different topologies and protocols uses in LAN
- Learn about simulating a LAN using ns2
Time Required
Around 3.00 hours
Local Area Network
A local area network (LAN) provides networking capability to a group of computers in close proximity to each other such as in an office building, a school, or a home. A LAN is useful for sharing resources like files, printers, games or other applications. A LAN is often connected to other LANs, which in turn are connected Internet.
LAN Topologies
Nodes in LAN are interconnected using one of four basic configurations:
- Bus topology
- Star topology
- Ring topology
- Mesh topology
Bus topology: In case of a bus topology, each machine is connected to a single cable through some kind of connector. Terminators (resistors) are required at each end of the bus cable to prevent the signal from bouncing back and forth on the cable.
Star topology: In local area networks with forming a star topology, each network host is connected to a central hub (a signal booster or repeater). In contrast to the bus topology, the star topology connects each node to the hub with a point-to-point connection. All traffic in the network has to pass through the central hub.
Ring Topology: In local area networks where the ring topology is used, each computer is connected to the network in form of a closed loop or ring. Each machine has a unique address for their identification. Ring topologies typically utilize a token passing scheme to control access to the medium. By utilizing this scheme, only one machine can transmit on the network at a time.
Mesh Topology: In a mesh network where all nodes are connected to each other through one or more hops.
MAC Protocols
Medium Access Control (MAC) protocols allows machines to access the communication medium, and thereby to "take turns" at transmitting data.
MAC protocols could be broadly classified into three types:
- Channel partitioning based protocols (TDMA, CDMA)
- Random access based protocols (ALOHA, CSMA)
- Taking turns (token passing, polling)
- Preamble: 7 bytes with pattern 10101010 followed by one byte with pattern 10101011. It is used to synchronize the receiver, sender.
- Addresses: Destination and source MAC address each 6 bytes long.
- Type: It indicates the higher layer protocol.
- CRC: Cyclic Redundancy Check is used for error detection, and correction to some extent.
- 10Base2: It is commonly called thin Ethernet. It operates at 10 Mbps and its maximum segment length is of 200m.
- 10Base5: Also known as thick Ethernet. It also operates at 10 Mbps, but could extend upto a maximum distance of 500m.
- 10BaseT: An Ethernet standard that transmits at 10 Mbps basebad signal over twisted wire pairs (telephone wire). Its maximum segment length is of 100m.
- 10BaseF: This kind of Ethernet use fiber optic cable. Its maximum segment length is of 200m.
- GbE: Gigabit Ethernet, which operates at 1000 Mbps.
- Link layer protocols such as ARQ
- MAC protocol
- Physical Channel
- A group of nodes which are to be connected to form a LAN
- Delay for the link
- Bandwidth of the link
- Link layer type e.g. "LL"
- Interfacing queue e.g."Queue Drop Tail"
- MAC layer type
- Channel type
Contention Based Protocol: Carrier Sense Multiple Access / Collision Detection (CSMA/CD)
In Carrier Sense Multiple Access with Collision Detection all work stations listen to the shared medium. If there is no ongoing transmission (by other devices), a workstation can transmit. However, if someone else is transmitting, the workstation backs off and waits. If two or more workstations sense that the medium is free, and start transmitting at the same time, a collision occurs! The end devices are however capable of detecting this collision (from the energy level of the medium), and they stop transmitting under such scenario. Each workstation waits for a random amount of time and tries again. CSMA/CD is non deterministic protocol. This works only on wired networks -- collisions can't be detected on a wireless network. CSMA/CA based protocols are used instead.
Taking turns
In this protocol each workstation takes turn in transmitting. A very common example is token ring LAN. Here a software token is passed from one device to the next. Token ring is an example of deterministic protocol.
Ethernet
Ethernet is the most popular CSMA/CD protocol. It is standardized as IEEE 802.3. In Ethernet when only one computer needs to transmit data, it can immediately (almost) access the line. However, when many computers want to access the medium frequently it generates a high traffic. This results in high average waiting time and higher chances of collision. In other words, when the size of a LAN increases, it's performance decreases. For example, an Ethernet network with more than 5% collision rate could indicate that the network is getting loaded. When the rate crosses 10%, the network could be considerably overloaded [v].
Ethernet Frame Structure
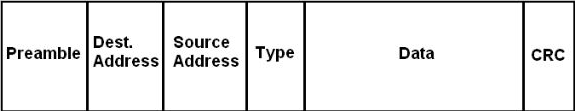 An Ethernet frame consists of the following fields:
An Ethernet frame consists of the following fields:
Ethernet Versions
Following are the different categories of Ethernet available commercially:
Simulating a LAN using Network Simulator 2
The network simulator simulates the three levels related to local area network. They are:
There are seven required parameters to setup a LAN with ns2:
The following code shows how to setup a LAN with three nodes forming a bus topology, CSMA/CD based MAC protocol and a DropTail queue attached to the link:
set lan [$ns newLan "$n3 $n4 $n5" 0.5Mb 40ms LL Queue/DropTail MAC/Csma/Cd Channel]
The nodes $n3, $n4, $n5 must be created as usual before the above statement could be executed. However, the above creates nodes of a different type: LanNode. This implementation of node helps to simulate the contention over a shared medium as found in a LAN [i, vi].

 Introduction
Introduction Theory
Theory Simulation
Simulation Self-evaluation
Self-evaluation Procedure
Procedure Exercises
Exercises References
References

